Security White Paper
Matlantis’ Efforts to Meet Security Requirements Based on ISO/IEC 27017
Introduction
Purpose of the Security White Paper
This Security White Paper (hereinafter referred to as “this document”) is intended to provide an understanding of Matlantis’ (hereinafter referred to as “the Service”) cloud security initiatives regarding the requirements specified in the international cloud security standard ISO/IEC 27017:2015, which requires information disclosure to customers.
Through this document, we aim to help customers better understand the cloud security measures of the Service, enabling them to utilize the Service more effectively to their benefit.
As the Service continuously evolves, please contact our sales team or refer to our website for the latest information.
Overview of the Service
The Service is a versatile atomic-level simulator that integrates traditional atomic simulators with deep learning models based on Neural Network Potential (NNP). This allows for the reproduction of material behavior at the atomic scale and facilitates large-scale material exploration.
ISMS Cloud Security Certification
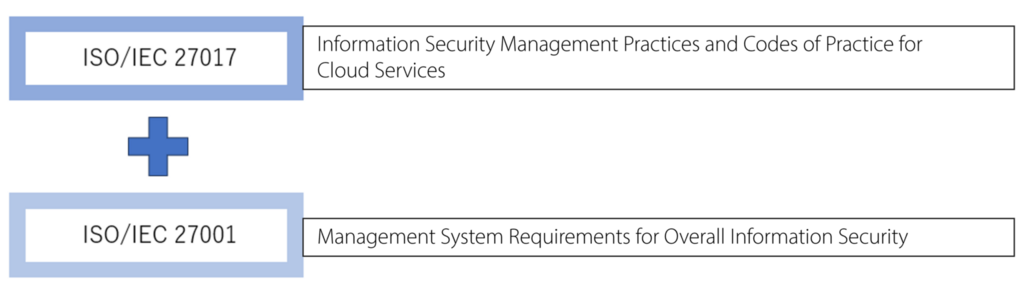
What is ISO/IEC 27017:2015?
The ISO/IEC 27000 series is an international standard for information security management established by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC).
Among this series, ISO/IEC 27017, issued in December 2015, serves as a guideline standard for managing information security in cloud services.
By reinforcing the efforts of ISO/IEC 27001, a general management system standard for information security, with ISO/IEC 27017, organizations can establish an information security management framework that also addresses the requirements of cloud services.
Cloud Security Measures
Explanation of Item Numbers
The item numbers listed below (e.g., 1.1 Policies for Information Security (ISO27017: 5.1.1)) refer to the clause numbers within ISO/IEC 27017, which outline the “Code of Practice for Information Security Controls” under Clauses 5 through 18 (excluding Clause 17).
1. Policies for Information Security
1.1 Policies for Information Security (ISO27017: 5.1.1)
As a cloud service provider delivering cloud services to customers, we have established the following information security policies, which are publicly available on our website:
2. Organization of Information Security
2.1 Roles and Responsibilities for Information Security (ISO27017: 6.1.1)
For the use of the Service, the roles and responsibilities between customers and our company are clearly defined in the “Matlantis Terms of Use” and the “Matlantis Service Specification.” Customers are required to agree to these terms before using the Service.
The “Matlantis Terms of Use” and “Matlantis Service Specification” are available on our website:
2.2. Contact with Authorities (ISO27017: 6.1.3)
Our company’s location is listed on our website: https://matlantis.com/ja/
The storage location of customers’ information assets is as follows:
- For customers in Japan: Data centers located in Japan.
- For customers in countries or regions other than Japan, authorized by us to use the Service: Data centers located in the United States, Europe (Germany), or Japan.
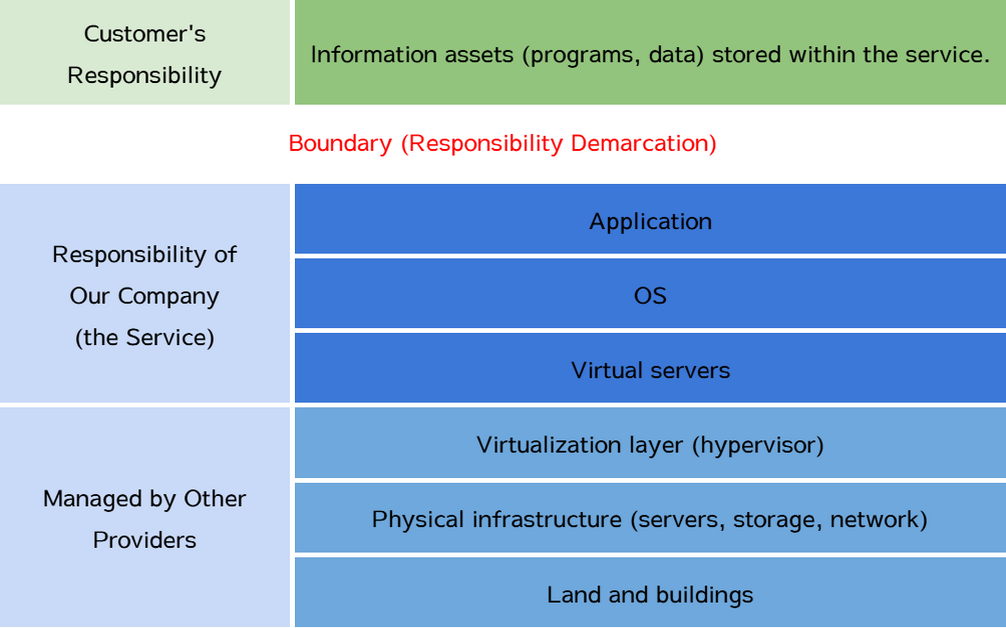
2.3 Shared Roles and Responsibilities in Cloud Computing Environments (ISO27017: CLD.6.3.1)
The outline of roles and responsibilities (responsibility boundaries) between customers and our company regarding the Service is as follows:
3. Human Resource Security
3.1 Awareness, Education, and Training for Information Security (ISO27017: 7.2.2)
To ensure our employees handle customers’ information assets appropriately and comply with information security rules, procedures, applicable laws, and regulatory considerations, we provide regular or as-needed training on information security.
4. Asset Management
4.1 Asset Inventory (ISO27017: 8.1.1)
We manage customer information assets separately from the information assets required to operate the Service, ensuring clear distinction and proper control.
4.2 Removal of Cloud Service Customer Assets (ISO27017: CLD.8.1.5)
When customers terminate their use of the Service, their information assets are appropriately deleted in accordance with Article 8 of the Matlantis Terms of Use.
Additionally, all customer information assets stored in the Service, including backups, are completely deleted within approximately one month of termination. Once deleted, the information assets cannot be recovered.
Therefore, customers are advised to back up their information assets as necessary before terminating the Service.
4.3 Information Labeling (ISO27017: 8.2.2)
The Service provides features for classifying and storing customer information assets, such as through “Group Drive” and “Team Drive.”
5. Access Control
5.1 User Registration and Deregistration (ISO27017: 9.2.1)
The Service allows administrators designated by customers to independently register, modify, or delete users through provided functionality.
5.2 User Access Provisioning (ISO27017: 9.2.2)
The Service assigns users as either administrators or general users and provides functionalities and procedures to manage these user roles.
5.3 Management of Privileged Access Rights (ISO27017: 9.2.3)
For login to the Service, we adopt an authentication method based on OpenID Connect (OIDC), ensuring a high-security level. Customers can select their preferred identity provider.
5.4 Management of User Secret Authentication Information (ISO27017: 9.2.4)
Customers are responsible for appropriately managing user accounts and secret authentication information for the Service.
5.5 Access Rights to Information (ISO27017: 9.4.1)
Access to customer information assets can be controlled by granting system administrator or general user privileges as needed.
5.6 Use of Privileged Utility Programs (ISO27017: 9.4.4)
The Service does not provide utility programs that bypass security procedures or enable the use of various service features.
5.7 Separation in Virtual Computing Environments (ISO27017: CLD.9.5.1)
The virtual environment utilized by customers is logically isolated using proven virtualization technologies.
5.8 Hardening of Virtual Machines (ISO27017: CLD.9.5.2)
In the virtual environment used by customers, features such as blocking external access, access monitoring, vulnerability management, and data encryption are implemented to enhance security levels.
6. Cryptography
6.1 Policy on the Use of Cryptographic Controls (ISO27017: 10.1.1)
The Service employs cryptographic security measures as follows:
- Files stored in Notebook Workspaces and Group Drives.
- Customer information assets stored in the internal Service database.
- Backups of the aforementioned information assets.
- All network communications within the Service (between customer environments and Matlantis environments, as well as within Matlantis itself).
7. Physical and Environmental Security
7.1 Secure Disposal or Reuse of Equipment (ISO27017: 11.2.7)
The disposal of storage devices and other equipment within the cloud vendor’s system environment is conducted in accordance with the disposal processes of each cloud vendor.
8. Operational Security
8.1 Change Management (ISO27017: 12.1.2)
For changes that may impact customers, prior notification is provided in the manner specified in the Service Specification.
Change histories are also managed and can be reviewed by customers within the Service.
8.2 Capacity Management (ISO27017: 12.1.3)
We continuously monitor resource usage related to the Service and maintain mechanisms to provide stable operations.
Additionally, customers can independently check the usage status of various resources.
8.3 Secure Operations by Practical Administrators (ISO27017: CLD.12.1.5)
The Service provides user manuals, including important operational procedures, for practical use.
8.4 Information Backup (ISO27017: 12.3.1)
Customer information assets are regularly backed up and properly stored:
- The Notebook workspace is snapshotted once a day and seven generations are retained.
- Files in Group Drive are backed up daily and seven generations are kept.
8.5 Event Log Collection (ISO27017: 12.4.1)
We collect various logs, including users’ last login dates, and can provide event logs upon customer request.
8.6 Clock Synchronization (ISO27017: 12.4.4)
Using the NTP service provided by the cloud vendor, the Service synchronizes time with the standard time of each region.
All timestamps recorded in the Service are based on this synchronized time.
8.7 Monitoring of Cloud Services (ISO27017: CLD.12.4.5)
The Service is continuously monitored, and we provide features that allow customers to review usage history for up to one month.
8.8 Management of Technical Vulnerabilities (ISO27017: 12.6.1)
Within our responsibility for the Service, we conduct regular vulnerability assessments and implement measures to maintain and improve security.
9. Communications Security
9.1 Network Separation (ISO27017: 13.1.3)
We ensure proper separation between customer network environments and other users’ network environments.
9.2 Alignment of Security Management for Virtual and Physical Networks (ISO27017: CLD.13.1.4)
The Service is delivered as a SaaS solution, leveraging the environment provided by IaaS cloud service vendors.
10. System Acquisition, Development, and Maintenance
10.1 Analysis and Specification of Information Security Requirements (ISO27017: 14.1.1)
The information security measures and functionalities implemented in the Service are described in this document.
Details of key security features can be found in the following sections:
- Access control functionalities
- Encryption functionalities
- Backup functionalities
- Log collection functionalities
10.2 Secure Development Policy (ISO27017: 14.2.1)
During development, we perform code reviews using processes such as automated testing and formatting tools to detect potential bugs, performance issues, and insecure coding patterns.
Additionally, when releasing new features that handle customer information assets, we conduct reviews by our internal security team.
Furthermore, third-party vulnerability assessments of web applications and platform diagnostics are conducted to ensure enhanced security.
11. Supplier Relationships
11.1 Addressing Security in Supplier Agreements (ISO27017: 15.1.2)
The Service is a SaaS-based cloud service, with details of responsibility demarcation outlined in Section 2.1: Roles and Responsibilities in Information Security.
Necessary security measures are implemented within the scope described in Section 2.1.
11.2 ICT Supply Chain (ISO27017: 15.1.3)
As a provider of SaaS cloud services, we utilize the cloud environment provided by IaaS cloud vendors to build our Service.
Thus, we serve as both a cloud service provider and a cloud service user within the supplier relationship.
In accordance with our Information Security Policy and Cloud Service Information Security Policy, we implement appropriate risk management measures for the components required from our cloud service providers.
12. Information Security Incident Management
12.1 Responsibilities and Procedures (ISO27017: 16.1.1)
If a major information security incident (e.g., customer information leakage) occurs within our scope of responsibility, we promptly and appropriately respond in accordance with our “Emergency Response Procedures.”
12.2 Reporting Information Security Incidents (ISO27017: 16.1.2)
If an information security incident occurs within our scope of responsibility, we notify customers using the methods outlined in the Matlantis Service Specifications.
Customers may report any security incidents related to the Service by contacting us through the inquiry email after logging into the Service.
12.3 Evidence Collection (ISO27017: 16.1.7)
If an information security incident occurs within our scope of responsibility and legal action is deemed possible, we preserve records and evidence and may disclose customer information assets to third parties as necessary.
13. Compliance
13.1 Identification of Applicable Laws and Contractual Requirements (ISO27017: 18.1.1)
Applicable laws for the use of the Service are specified in Article 18 of the Matlantis Terms of Use, which stipulates that Japanese law applies.
We also identify and comply with laws and regulations relevant to the countries and regions where the Service is provided.
13.2 Intellectual Property Rights (ISO27017: 18.1.2)
The intellectual property rights belonging to customers are defined in Article 7 of the Matlantis Terms of Use.
13.3 Protection of Records (ISO27017: 18.1.3)
Records related to information security are managed appropriately to prevent loss, destruction, or alteration, in accordance with laws, regulations, contracts, and business requirements.
13.4 Regulations on Encryption Functions (ISO27017: 18.1.5)
Encryption functions comply with relevant laws and regulations, including the Foreign Exchange and Foreign Trade Act.
13.5 Independent Review of Information Security (ISO27017: 18.2.1)
The Service is certified, maintained, and updated for compliance with ISO27001 and JIP-ISMS517 (ISO27017) through third-party audits, demonstrating our commitment to information security.
Initial Version: July 1, 2024
Revised on December 3, 2024 (reflecting points raised during the ISO certification audit)
Revised on December 15, 2025 (to reflect findings from ISO certification surveillance audits)